Openssl Generate Key From Pem
.pem SSL Creation Instructions
SSL .pem files (concatenated certificate container files), are frequently required for certificate installations when multiple certificates are being imported as one file.
In this case, you can generate a new self-signed certificate that represents a Common Name your application can validate. This topic tells you how to generate self-signed SSL certificate requests using the OpenSSL toolkit to enable HTTPS connections. The private key is generated and saved in a file named 'rsa.private' located in the same folder. Generating the Public Key - Linux 1. Open the Terminal. Type the following: openssl rsa -in rsa.private -out rsa.public -pubout -outform PEM 2. The public key is saved in a file named rsa.public located in the same folder.
OpenSSL – How to convert SSL Certificates to various formats – PEM CRT CER PFX P12 & more How to use the OpenSSL tool to convert a SSL certificate and private key on various formats (PEM, CRT, CER, PFX, P12, P7B, P7C extensions & more) on Windows and Linux platforms. Using openssl, I've created a private key as follows: openssl genrsa -out myKey.pem Then, to generate the csr demanded by the CA, I've executed the following: openssl req -new -key myKey.pem -out cert.csr The CA responded with a certificate which I stored in a file named myCert.cer.
- Openssl can turn this into a.pem file with both public and private keys: openssl pkcs12 -in file-to-convert.p12 -out converted-file.pem -nodes A few other formats that show up from time to time:.der - A way to encode ASN.1 syntax in binary, a.pem file is just a Base64 encoded.der file.
- Create a pkcs12 (.pfx or.p12) from OpenSSL files (.pem,.cer,.crt.) You have a private key file in an openssl format and have received your SSL certificate. You'd like now to create a PKCS12 (or.pfx) to import your certificate in an other software? Here is the procedure!
This article contains multiple sets of instructions that walk through various .pem file creation scenarios.
Visio premium 2010 product key generator. Creating a .pem with the Entire SSL Certificate Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt), Root (TrustedRoot.crt), and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Server and Intermediate Certificates
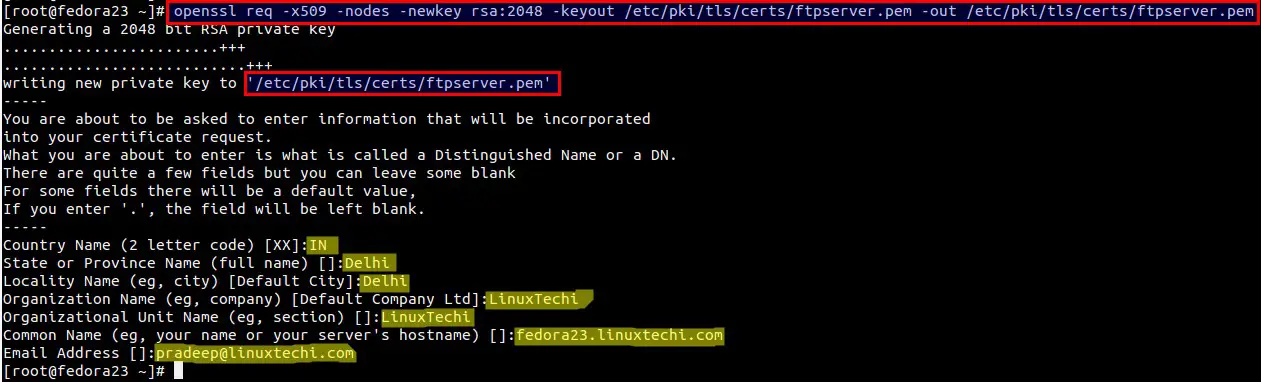
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Private Key and Entire Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Private Key - your_domain_name.key
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN RSA PRIVATE KEY-----
(Your Private Key: your_domain_name.key)
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Keys are the basis of public key algorithms and PKI. Keys usually come in pairs, with one half being the public key and the other half being the private key. With OpenSSL, the private key contains the public key information as well, so a public key doesn’t need to be generated separately.
Public keys come in several flavors, using different cryptographic algorithms. The most popular ones associated with certificates are RSA and DSA, and this article will show how to generate each of them.
Generating an RSA key
Openssl Generate Key From Pem File
A RSA key can be used both for encryption and for signing and generating a key is quite easy, all you have to do is the following:
That will generate a private key with is password protected (it will prompt you for the password during generation). If you don’t want it password protected (usually for server side use) then leave the -des3 parameter out, i.e.:
Generating a DSA key
A DSA key can be used for signing only. This is important to keep in mind to know what kind of purposes a certificate request with a DSA key can really be used for.
Generating a key for the DSA algorithm is a two-step process. First, you have to generate parameters from which to generate the key then to generate the key itself.
Again like RSA, 2048 is the size of the key, in bits with anything smaller than 2048 being insecure in todays standards.
Openssl Generate Key From Pem Mac
Also the -des3 parameter will prompt you for a pass phrase – for server use leave it out: