Openssl Generate Csr With Existing Key
The following instructions will guide you through the CSR generation process on Apache OpenSSL. To learn more about CSRs and the importance of your private key, reference our Overview of Certificate Signing Request article. If you already generated the CSR and received your trusted SSL certificate, reference our SSL Installation Instructions and disregard the steps below.
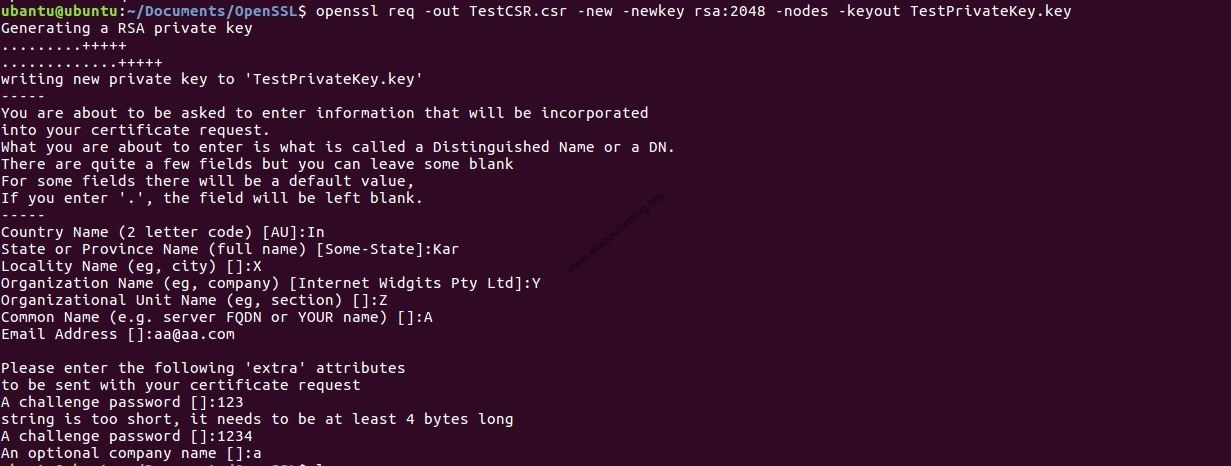
In order to gain some time, you can now generate your command line with our CSR creation assistant tool. Just copy/paste to finalize! To install a certificate on Apache Windows, you will need a cryptographic tool to generate the private key and the CSR. To do so, you can use 'OpenSSL': Install OpenSSL on a Windows computer. 1- Generate the. $ openssl req -out codesigning.csr -key private.key -new Where private.key is the existing private key. As you can see you do not generate this CSR from your certificate (public key). Also you do not generate the 'same' CSR, just a new one to request a new certificate. The CSR has all of the requested details of the certificate (Subject name, location, organization, etc.) along with the public key. The private key however is stored on the machine that generated the CSR (presumably the server requiring the cert, but not necessarily) and is NOT included in the contents of the CSR, and may not be derived from. Use the following command to generate the CSR: openssl req -new -sha256 -key fabrikam.key -out fabrikam.csr When prompted, type the password for the root key, and the organizational information for the custom CA: Country, State, Org, OU, and the fully qualified domain name. This is the domain of the website and it should be different from the. $ touch myserver.key $ chmod 600 myserver.key $ openssl req -new -config myserver.cnf -keyout myserver.key -out myserver.csr This will create a 2048-bit RSA key pair, store the private key in the file myserver.key and write the CSR to the file myserver.csr. The private key is stored with no passphrase.
$ openssl req -out CSR.csr -new -newkey rsa:2048 -nodes -keyout privateKey.key Generate a certificate signing request (CSR) for an existing private key $ openssl req -out CSR.csr -key privateKey.key -new In the above you'll notice the use of the privateKey.key from the previous step being used to create the CSR. Openssl cheatsheet.
1. Log In
Log in to your server’s terminal via Secure Shell (SSH).
2. Run CSR Generation Command
Generate a private key and CSR by running the following command:Here is the plain text version to copy and paste into your terminal:
Note: Replace “server” with the domain name you intend to secure.
3. Enter your Information
Enter the following CSR details when prompted:
- Common Name: The FQDN (fully-qualified domain name) you want to secure with the certificate such as www.google.com, secure.website.org, *.domain.net, etc.
- Organization: The full legal name of your organization including the corporate identifier.
- Organization Unit (OU): Your department such as ‘Information Technology’ or ‘Website Security.’
- City or Locality: The locality or city where your organization is legally incorporated. Do not abbreviate.
- State or Province: The state or province where your organization is legally incorporated. Do not abbreviate.
- Country: The official two-letter country code (i.e. US, CH) where your organization is legally incorporated.
Note: You are not required to enter a password or passphrase. This optional field is for applying additional security to your key pair.
4. Copy the CSR text from the file
Locate and open the newly created CSR in a text editor such as Notepad and copy all the text including:
Note 1: Your CSR should be saved in the same user directory that you SSH into unless otherwise specified by you. Note 2: We recommend saving or backing up your newly generate “.key” file as this will be required later during the installation process.
5. Generate the order
Return to the Generation Form on our website and paste the entire CSR into the blank text box and continue with completing the generation process.
Upon generating your CSR, your order will enter the validation process with the issuing Certificate Authority (CA) and require the certificate requester to complete some form of validation depending on the certificate purchased. For information regarding the different levels of the validation process and how to satisfy the industry requirements, reference our validation articles. /fake-windows-8-product-key-generators.html.

After you complete the validation process and receive the trusted SSL Certificate from the issuing Certificate Authority (CA), proceed with the next step using our SSL Installation Instructions for Apache OpenSSL.
Was this article helpful?
Related Articles
In this article you’ll find how to generate CSR (Certificate Signing Request) using OpenSSL from the Linux command line, without being prompted for values which go in the certificate’s subject field.
Below you’ll find two examples of creating CSR using OpenSSL.
In the first example, i’ll show how to create both CSR and the new private key in one command.
And in the second example, you’ll find how to generate CSR from the existing key (if you already have the private key and want to keep it).
Both examples show how to create CSR using OpenSSL non-interactively (without being prompted for subject), so you can use them in any shell scripts.
Create CSR and Key Without Prompt using OpenSSL
Use the following command to create a new private key 2048 bits in size example.key and generate CSR example.csr from it:
| Option | Description |
|---|---|
| openssl req | certificate request generating utility |
| -nodes | if a private key is created it will not be encrypted |
| -newkey | creates a new certificate request and a new private key |
| rsa:2048 | generates an RSA key 2048 bits in size |
| -keyout | the filename to write the newly created private key to |
| -out | specifies the output filename |
| -subj | sets certificate subject |
Generate CSR From the Existing Key using OpenSSL
Use the following command to generate CSR example.csr from the private key example.key:
| Option | Description |
|---|---|
| openssl req | certificate request generating utility |
| -new | generates a new certificate request |
| -key | specifies the file to read the private key from |
| -out | specifies the output filename |
| -subj | sets certificate subject |
Automated Non-Interactive CSR Generation
The magic of CSR generation without being prompted for values which go in the certificate’s subject field, is in the -subj option.
| -subj arg | Replaces subject field of input request with specified data and outputs modified request. The arg must be formatted as /type0=value0/type1=value1/type2=…, characters may be escaped by (backslash), no spaces are skipped. |
The fields, required in CSR are listed below:
Openssl Generate Csr With Existing Key West
| Field | Meaning | Example |
|---|---|---|
| /C= | Country | GB |
| /ST= | State | London |
| /L= | Location | London |
| /O= | Organization | Global Security |
| /OU= | Organizational Unit | IT Department |
| /CN= | Common Name | example.com |
You’ve created encoded file with certificate signing request.
Openssl Generate Csr With San
Now you can decode CSR to verify that it contains the correct information.